What Is Cloud Access Security Broker And How Does It Work? Cloud computing services are critical to many businesses, but they also serve as attractive targets for hackers looking for sensitive company information. A cloud access security broker adds another layer of online security, protecting information while keeping cybercriminals at bay. Learn more about Cloud Access Security Broker and how it protects data. Then, get dependable cybersecurity software to safeguard all of your devices.
What exactly is a Cloud Access Security Broker?

A cloud access security broker (CASB), according to Gartner, is a cloud-based or on-premises security policy enforcement point that’s also placed between cloud service providers and cloud service consumers to combine and interject enterprise security measures as cloud-based resources are accessed. Consider the CASB to be the sheriff who enforces the rules established by the cloud service administrators.
Organizations are increasingly relying on CASB vendors to enforce security policies, resolve cloud service risks, and comply with regulations, even when cloud services are located outside their perimeter and are not directly under their control.
The CASB’s four pillars
Four essential components are required for effective cloud access security brokerage. These components work together to provide a strong cloud security solution.
Let us now examine the four pillars of Cloud Access Security Broker:
Threat defense
Using cloud services, malware as well as other online threats can be easily introduced and spread throughout a company. Effective CASB solutions include malware but also virus removal tools as well as real-time threat protection. They are capable of scanning and targeting threats across both internal and external systems, as well as preventing unauthorized access to a company’s cloud data and services.
Compliance
Compliance standards, as to if voluntary or legal regulations are critical for an organization’s integrity and reputation. Unauthorized utilization of cloud tools makes data mishandling all too easy. By enforcing data policies, CASB tools aid in the enforcement of compliance standards in cloud services.
Data safety
Cloud access security brokers offer broader data protection than email security or other, more focused tools. CASBs detect sensitive data traffic to and from the cloud, alerting IT to any important consideration in determining. A CASB also conducts threat observation research, assisting in the detection and prevention of illicit behavior before it escalates.
Visibility
Companies may have difficulty maintaining track of sensitive data in the cloud, raising the likelihood of data leakage — especially because most cloud services lack auditing as well as logging functions. By tracking but also highlighting data points and transfers, CASBs improve data visibility and management.
How does Cloud Access Security Broker function?
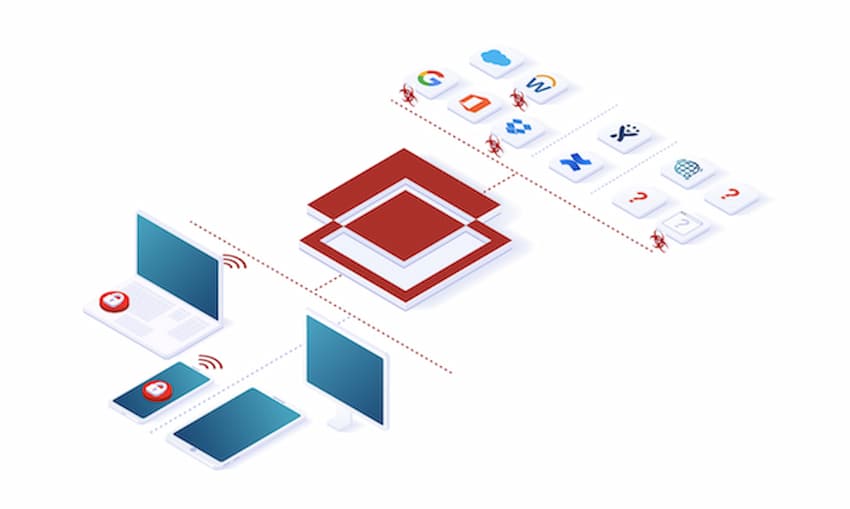
A CASB’s primary functions are to protect data, control cloud usage, and prevent malware threats. To accomplish this, CASBs must go through a specific process that includes inventory as well as categorization of cloud usage, and also proactive data protection.
In practice, CASB software works as follows:
- Auto-discovery tools are used by CASBs to inventory all cloud-service use within a company, including both sanctioned as well as unsanctioned usage.
- The CASB then evaluates the risk level of each cloud service in use. It will determine the tool’s functionality, assess the information exchanged, and evaluate how and where the information is distributed.
- Remediation: The data collected during discovery as well as classification is used by cloud access security brokers to set user access rules, create policies for company data, and respond to violations.
The Advantages of Cloud Access Security Broker
For large businesses that handle massive amounts of customer data as well as sensitive financial information, going to rely on basic cybersecurity tools for removing malware or viruses and using a VPN isn’t enough to keep up with today’s most dangerous hackers. CASBs address specific security vulnerabilities in businesses that use cloud-based services.
The following are the primary advantages of CASBs:
- Governance but also risk management in the cloud
- Data loss prevention in the workplace
- Control sharing and collaboration
- Malware detection and prevention
- Key management and data encryption
- Access management
Read more: How To Wake Up Laptop with 4 Best Methods We Guide Below
Choosing a CASB
Once you know which cloud services your company utilizes, you can consider which CASB best suits your business operations as well as other specific requirements.
Here are 3 things to consider when selecting a CASB:
What am I looking for in a Cloud Access Security Broker?
Take into account the cloud computing services that your company uses and what you want from a CASB. To help you focus your needs, consult with internal stakeholders as well as ask for input from cybersecurity analysts and business consultants.
Will my Cloud Access Security Broker be able to adapt to changes?
Cybersecurity environments are constantly changing as technology advances, particularly with the use of the cloud. Well-known CASBs such as Gartner and Bitglass stay current by updating cloud security and compliance policies.
Will my CASB safeguard IaaS?
Although SaaS protection is popular, IaaS environments are also protected by comprehensive enterprise security. Consider a CASB that protects not only IaaS activity and configurations, but also customers through threat protection as well as activity monitoring.
